If a user has multiple embedded wallets (e.g. on different blockchains, or multiple HD addresses),
enrolling in MFA will require MFA for signatures and transactions from any of them.
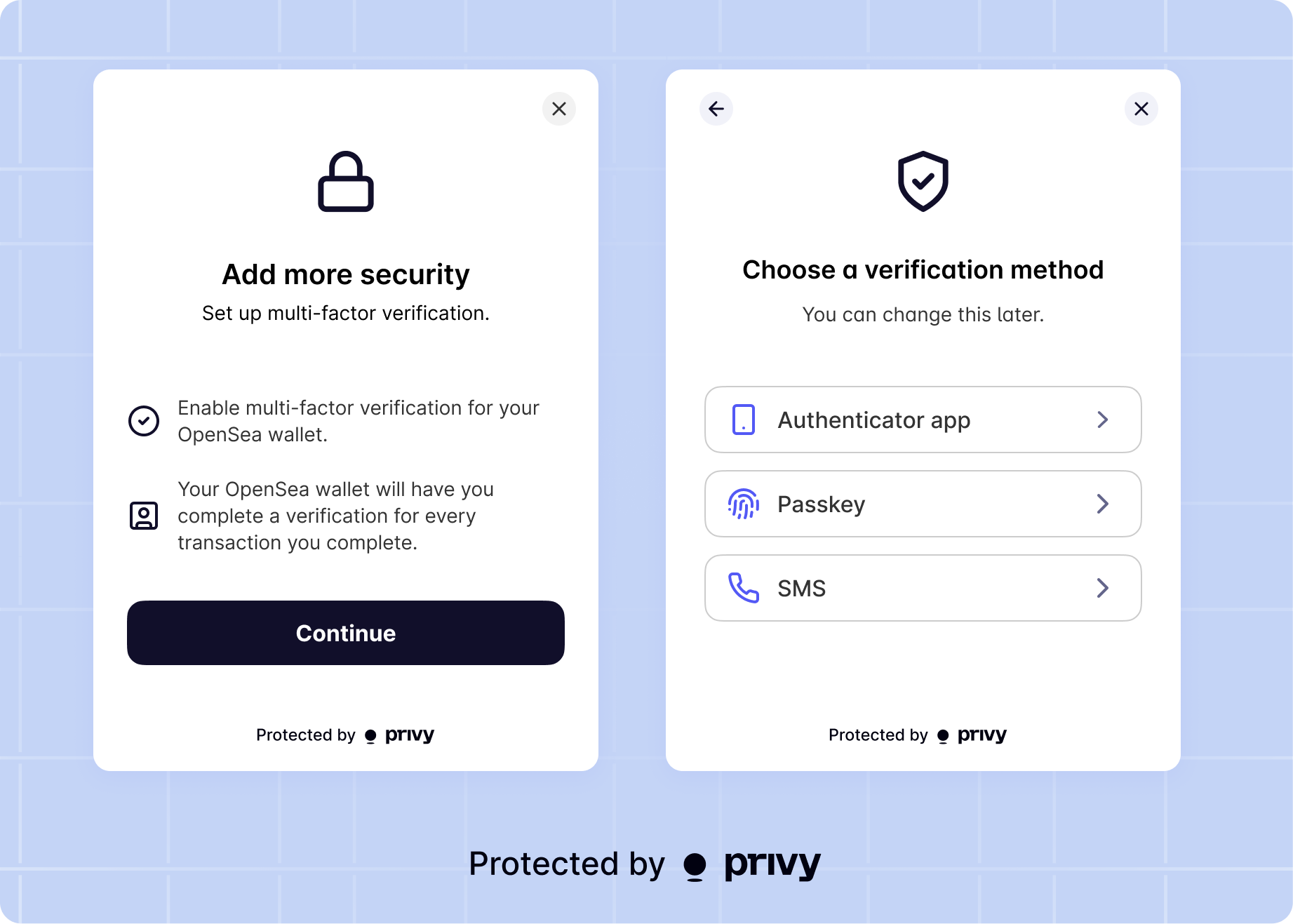
- SMS, where users verify with a 6-digit MFA code sent to their phone number
- Time-based one-time password (TOTP), where users verify with a 6-digit MFA code from an authentication app, like Authy or Google Authenticator
- Passkeys, where users verify with a previously registered passkey, generally through biometric authentication on their device
Policy-based MFA with Policies
By default, once a user enrolls in MFA, all wallet actions require MFA verification. However, you can implement policy-based MFA to require MFA only for specific actions while allowing routine transactions to proceed without additional verification. For example, you can:- Require MFA only for transactions above a certain amount (e.g., transfers over 1000 USDC)
- Require MFA for withdrawals while allowing deposits without MFA
- Apply MFA requirements based on specific tokens, contracts, or actions
Learn how to implement policy-based MFA in our policy-based MFA
recipe.

