Security without compromise
Privy wallets are designed with security at their core. Our approach uses a combination of key splitting (Shamir’s secret sharing) and private key reconstitution in secure execution environments to ensure that only authorized parties can access their wallets. Wallets remain fully non-custodial and users ultimately have full control over their assets.Flexible owner configurations
Privy’s control model allows you to specify exactly who can approve different types of actions. Quorums can include users, authorization keys, or both, enabling patterns such as:- User-controlled wallets: The user approves everything.
- Delegated permissions: Users grant limited, scoped authorization to the application.
- Application-managed control: Services approve operational actions under strict policies.
- Shared control: Multiple parties must sign off on sensitive operations.
Programmable policies
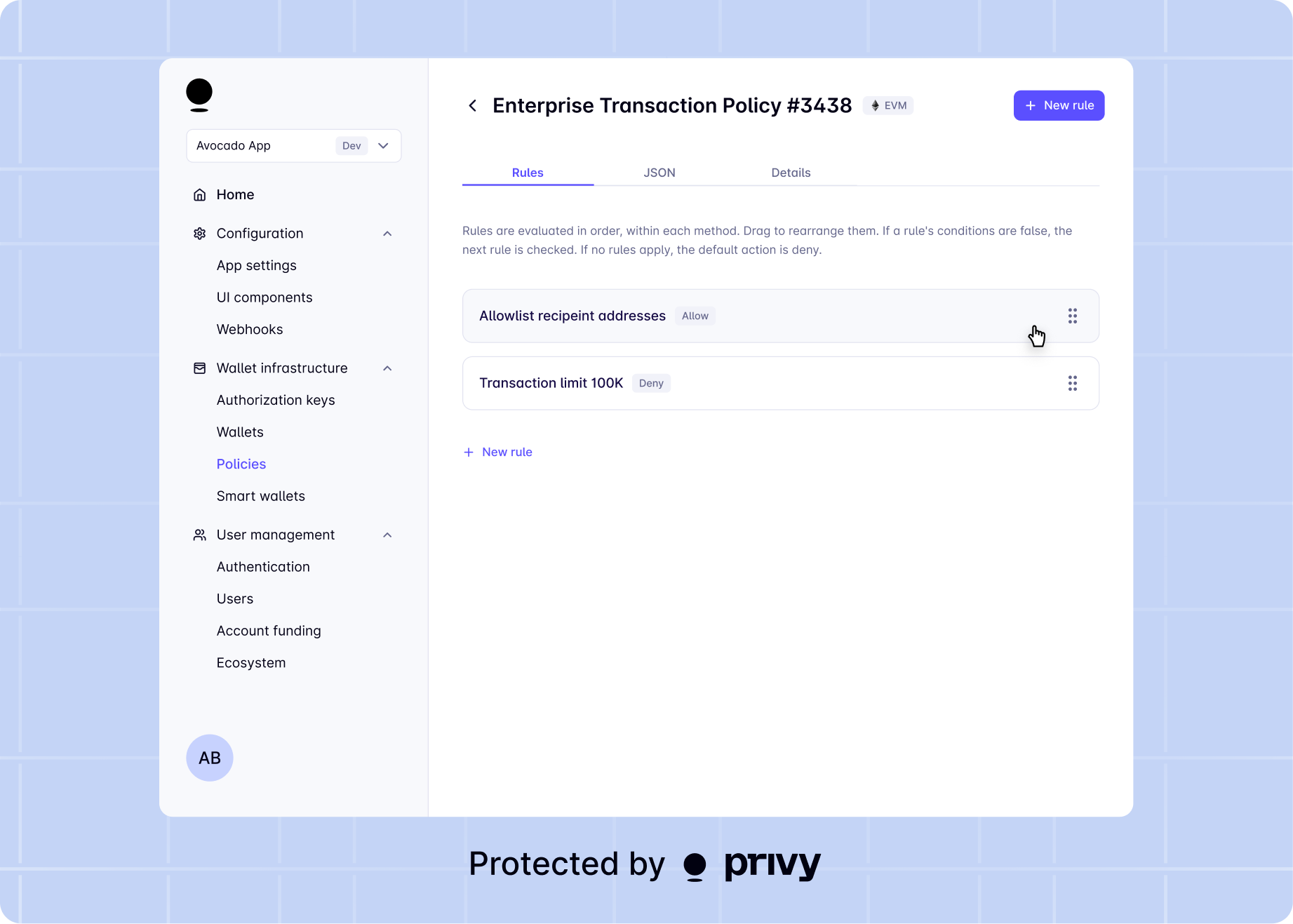
Policies define the actions a wallet is allowed to take. They operate as key-level enforceable guardrails, ensuring wallets behave only as your application intends. By default, the trusted execution environment (secure enclave) enforces policies when processing wallet actions, such as signature requests, transactions, and key export. The enclave evaluates policy rules in a tamper-proof environment before any operations proceed. Privy enforces some policies at the API level. For example, limiting transfer sizes requires transaction simulation which runs outside the enclave today.- Transaction limits: Set maximum amounts that can be transferred.
- Approved destinations: Specify recipients where funds can be sent.
- Contract interactions: Control which smart contracts can be used.
- Action parameters: Define what specific operations are permitted.