Privy’s wallet API is secured with tamper-proof cryptographic authorization and a powerful, intuitive policy engine. This means that the trusted execution environment (secure enclave) will only act on requests issued by authorized parties, and only specific permitted actions may be processed.
Privy wallets are non-custodial and have a fully programmable control model. Privy’s flexible
configuration enables the full custody spectrum from user-custodial wallets to powerful
service-controlled accounts.
Authentication and authorization
Authorization keys
Requests to Privy wallet API endpoints are protected by authorization keys. This requires the secure enclave to verify a signature from the required authorization key before executing any requests. Learn more
Privy uses P-256 (also known as secp256r1) asymmetric keys for authorization keys. When you register a key:
- The private key is generated on your device, and is only ever known to your app. Neither Privy nor the enclave ever sees the P-256 private key, and cannot sign payloads with it.
- The public key is registered with the enclave, and is used to verify signatures produced by your servers.
The authorization signature is a signature generated over the body and all critical parameters of each request. This authorization signature guarantees the enclave only processes verified requests. The enclave verifies the signature against the corresponding authorization public key registered for the wallet before executing any wallet actions.
Powerful, flexible controls
Authorization keys enable a fully configurable control model for wallets. This includes the full spectrum from user-custodial wallets to powerful service-controlled accounts.
When you create a wallet, you specify its owner, which is the key (or key quorum) that controls the wallet. By default, this key is also required to authorize wallet actions, such as generating signatures or transacting funds.
This wallet ownership model is extremely flexible. It enables you to configure, e.g:
- Fully user self-custodial wallets, using an authorization key tied to the user’s authentication method as the authorization key
- Fully user self-custodial wallets, using the user’s passkey as the authorization key
- Service-controlled wallets, using an authorization key that is held by your service
- Multi-sig wallets, using a quorum of authorization keys held by different parties
Key quorums
Privy enables your app to require quorum approvals on wallet actions, so that signatures from m-of-n authorization keys are required in order to take action using the wallet. Key quorums are defined by a list of authorization public keys and a threshold required for approval. Learn more
Multi-factor authentication
Privy enables native multi-factor authentication for wallet actions. This means your app can require additional verification for sensitive wallet operations using:
- Authenticator apps (TOTP)
- Biometric verification (passkeys)
- SMS confirmation
- Hardware security keys
Multi-factor authentication is enforced via authenticated signers. Learn more about configuring multi-factor authentication for your app here.
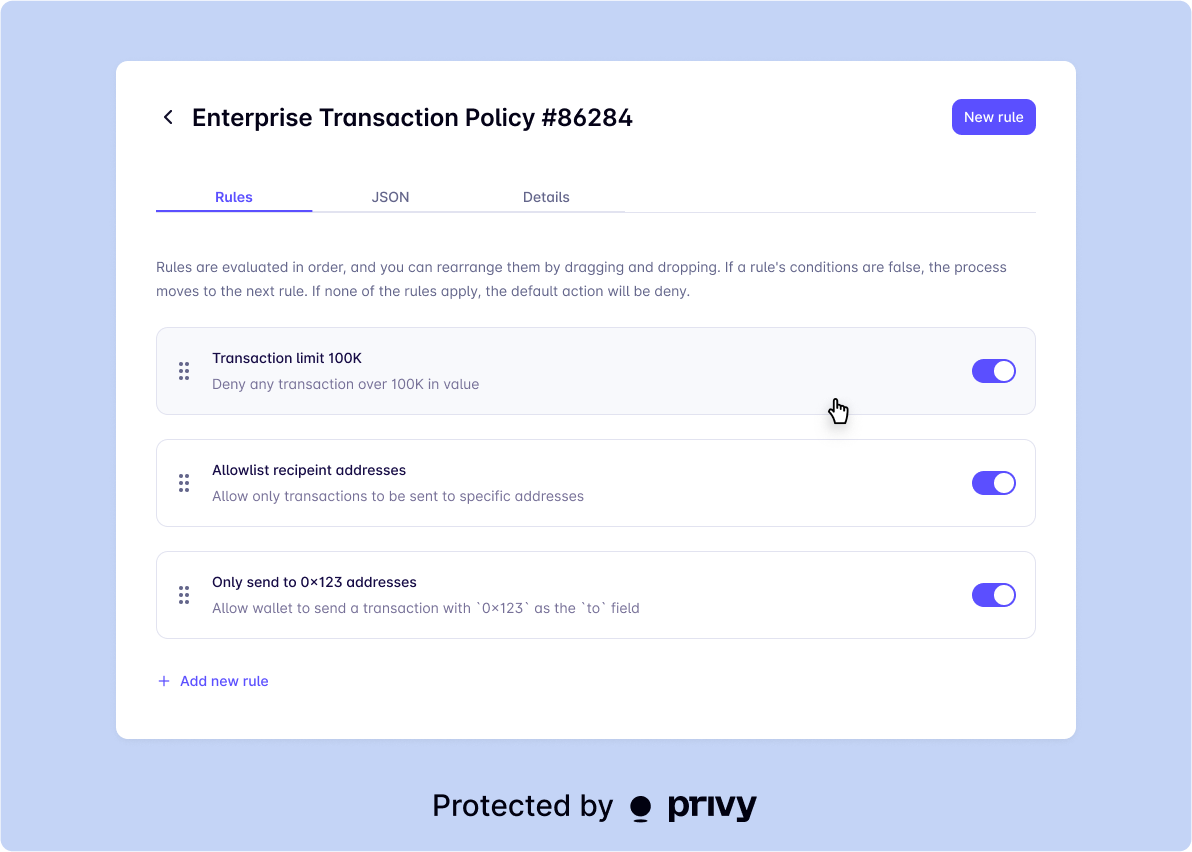
Policies
Privy’s policy engine allow your application to restrict the actions that can be taken with wallets. This is important for features such as payment subscriptions, stop and limit orders, or scheduled transactions.
Policies allows you to configure transfer limits, allowlists and denylists of transfer recipients, allowlists and denylists of smart contracts and programs, and even constraints around calldata that can be passed to smart contracts.
By default, policies are enforced by the trusted execution environment as part of processing wallet actions, such as signature requests, transactions, and key export. Some policies are enforced at the API level. For example, limiting transfer sizes requires transaction simulation which runs outside the enclave today.
This ensures that wallets can only ever be used to take actions your application intends to take.
Learn more about configuring policies here.